Preempt researchers have discovered two vulnerabilities that may allow attackers to bypass a number of protections and mitigations against NTLM relay attacks and, in some cases, to achieve full domain compromise of a network.
What is NTLM?
NT LAN Manager (NTLM) is an authentication protocol developed by Microsoft, used to authenticate a client to resources on an Active Directory domain.
Fast online lm hash cracking. Use browser with frames support. Powershell Empire? - likely a MS SQL Server Service Account), any AD user can request a krb5tgs hash from it which can be used to crack the password. Based on my benchmarking, KRB5TGS cracking is 28 times slower than NTLM.
“Interactive NTLM authentication over a network typically involves two systems: a client system, where the user is requesting authentication, and a domain controller, where information related to the user’s password is kept,” Microsoft explains.
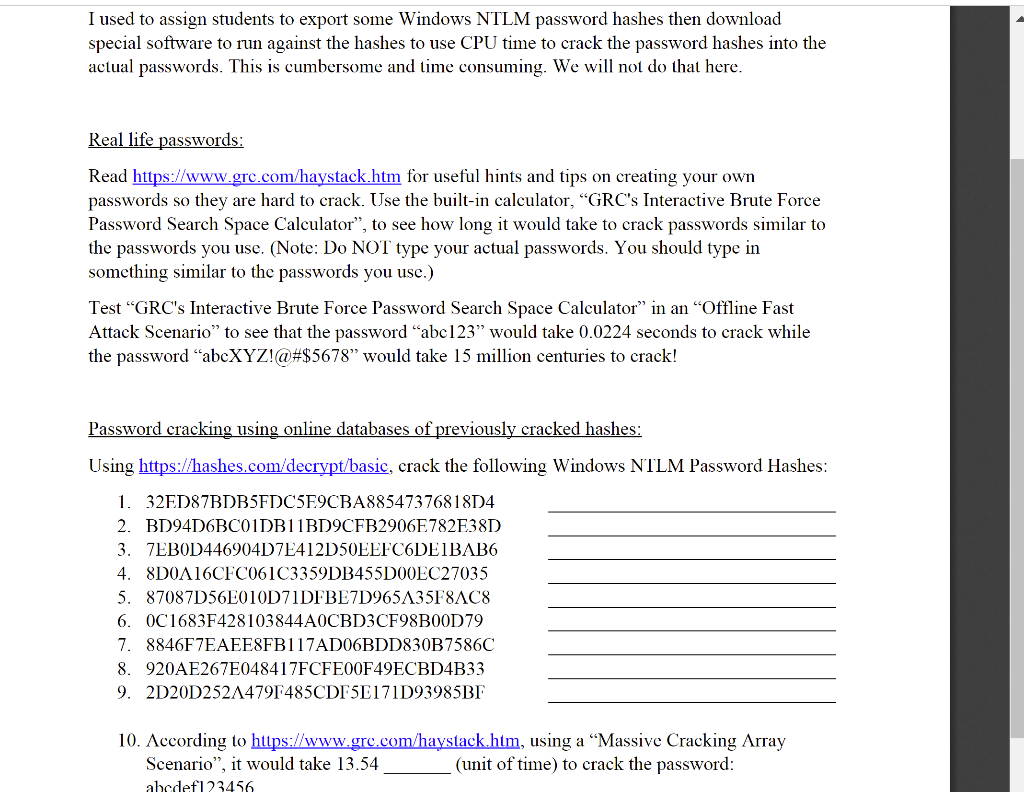
“NTLM credentials are based on data obtained during the interactive logon process and consist of a domain name, a user name, and a one-way hash of the user’s password. NTLM uses an encrypted challenge/response protocol to authenticate a user without sending the user’s password over the wire. Instead, the system requesting authentication must perform a calculation that proves it has access to the secured NTLM credentials.”
While effectively superseded by Kerberos, NTLM is still enabled on enterprise Windows systems to maintain compatibility with older systems.
Unfortunately, it is often targeted by attackers seeking to compromise the Active Directory (AD) infrastructure, usually via NTLM relay attacks. NTLM relay attacks hinge on getting valid NTLM credentials from the client and using them to create admin accounts on the target local network’s domain controller.
About the vulnerabilities
CVE 2019-1166 allows attackers to bypass the MIC (Message Integrity Code) protection on NTLM authentication and modify any field in the NTLM message flow, including the signing requirement.

“This bypass allows attackers to relay authentication attempts which have successfully negotiated signing to another server, while tricking the server to entirely ignore the signing requirement. All servers that do not enforce signing are vulnerable to this attack,” the researchers shared.
CVE 2019-1166 is effectively a different way to achieve the same thing that Preempt researchers found possible through CVE-2019-1040, which was fixed by Microsoft in June 2019.
The second flaw – CVE 2019-1338 – “allows attackers to bypass the MIC protection, along with other NTLM relay mitigations such as Enhanced Protection for Authentication (EPA) and target SPN validation for certain old NTLM clients that are sending LMv2 challenge responses.”
According to the researchers, (MitM) attackers could use it to authenticate to critical servers such as OWA and ADFS and steal user data.

What can enterprises do to protect their network?
Lm Hash Crack
Microsoft has released security updates (rated “Important”) that plug both of these holes as part of the October 2019 Patch Tuesday batch.
Ntlm Hash Decoder
The researchers advised admins to implement the patches, enforce NTLM mitigations (server signing and EPA), apply NTLM relay detection and prevention techniques, monitor NTLM traffic in their network (and try to restrict insecure NTLM traffic), get rid of clients sending LM responses and, in general, to try to reduce NTLM usage in their network as much as possible.
Lm Hash Cracker Online
This Rainbow cracking technology works on simple concept. Instead of computing the hashes for each password dynamically and comparing with the correct one during cracking, password hashes are computed in advance for all character sets. These hashes are then stored in datasets called rainbow tables.
So cracking involves just comparing the current password hash with the pre computed hashes within the rainbow tables and get the associated plain text password. Hence it takes very less time compared to the traditional method of brute force cracking. Setting up the rainbow table for various character sets is just one time activity and may take days or months based on the character set and speed of the machine. Once the rainbow tables are ready, you can feed the password hash to it and get your password cracked in seconds.
